Honeytokens on every endpoint. Within minutes.
With Honeyhack you can super easily deploy and manage honeytokens on thousands of machines
Improve your cyber-defense with honeytokens
Multiple reports are stating that intrusions are detected too late; on average it takes around 197 days to know that a breach of your system has happened. Honeytokens are a dead-simple way to trick intruders into fake crown-jewels.
Reduce Mean Time To Detect (MTTD)
Increase likelyhood of detecting
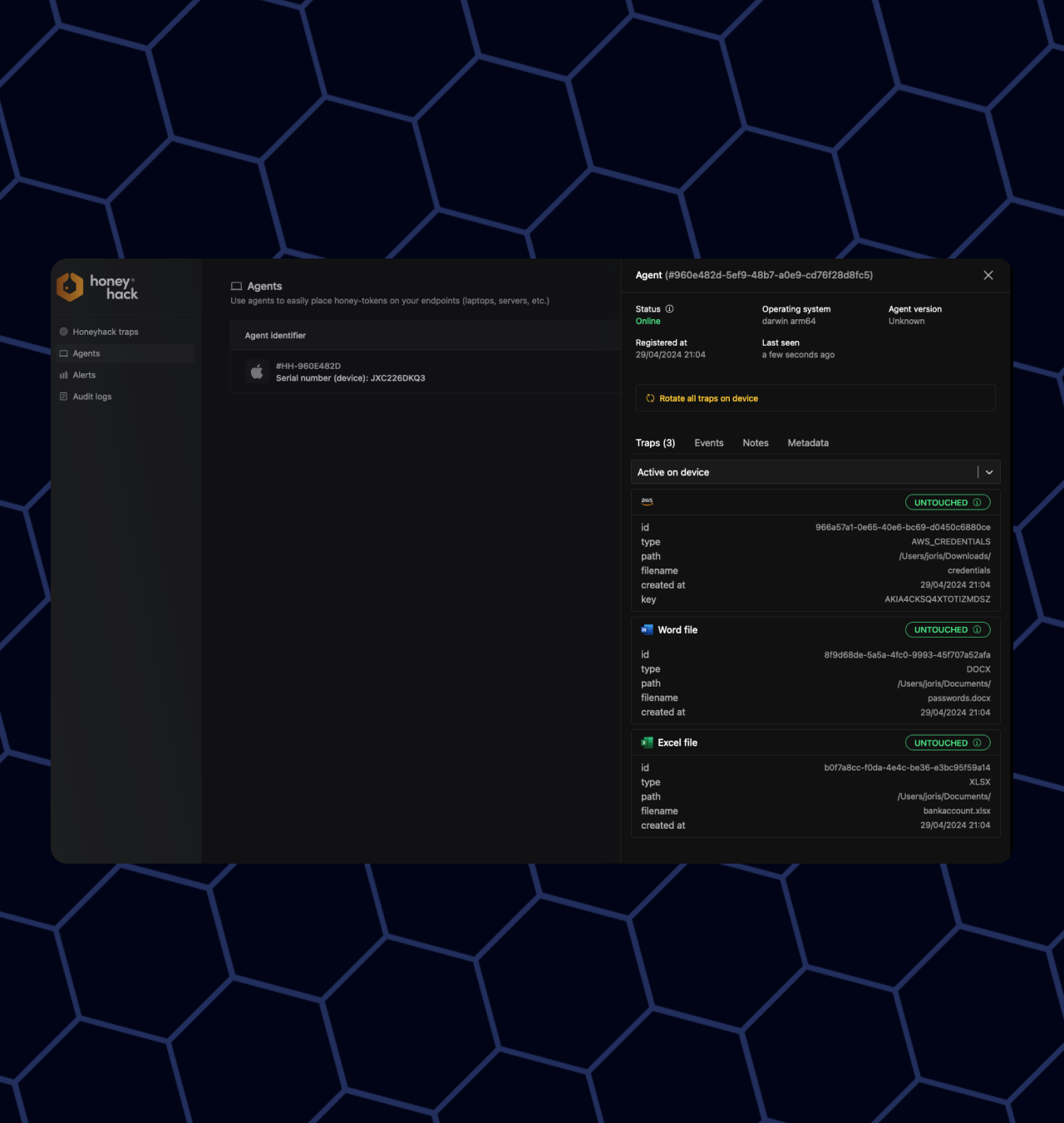
Deploy honeytokens to thousands of endpoints in minutes
The Honeyhack-Agent allows you to sprinkle honeytokens on all your laptops in minutes, that way the chance of detecting an intrusion or bad-actor will be bigger.

Word
A Word honeytoken is a specially crafted document that acts as a decoy to lure potential attackers. Think about "Bankstatement.docx" or "Backup-procedure-database.docx". It's designed to trigger alerts when opened with Word.
.svg.png)
Excel
An Excel honeytoken is a meticulously constructed spreadsheet file, such as "Financial-Report.xlsx" or "Passwords.xlsx" strategically placed to attract malicious actors.

AWS Credential
An AWS honeytoken is a real credential to a fake AWS-organization that will report back to you when somebody used that credential to gain access.

SSH-keys (coming soon)
SSH-honeytokens are SSH-keys that attackers are interested in, since they gain shell-access to servers. When attackers use Honeyhack's SSH-keys, you will be notified.

Wireguard VPN (coming soon)
Wireguard is often used by companies as a VPN protocol. The Wireguard honeytoken is a VPN-config that will trigger an alert when used. Attackers might be interested in this because they might gain some access to a resource using that VPN.

PostgreSQL (coming sooon)
Databases are often the crown-jewels for bad-actors, valuable customer-data or business-data resides there. With the PostgreSQL-token the attacker will probably try to connect to a database, but he will not know that you will be notified.
The easiest way for honeytoken creation, deployment and management
Honeytokens on all your endpoints
✅ No more scripting against your MDM: Install the Honeyhack-agent and honeytokens will automatically be placed at strategic locations on your endpoints.
✅ Support for all major operating-systems.

Central management of all your tokens & agents
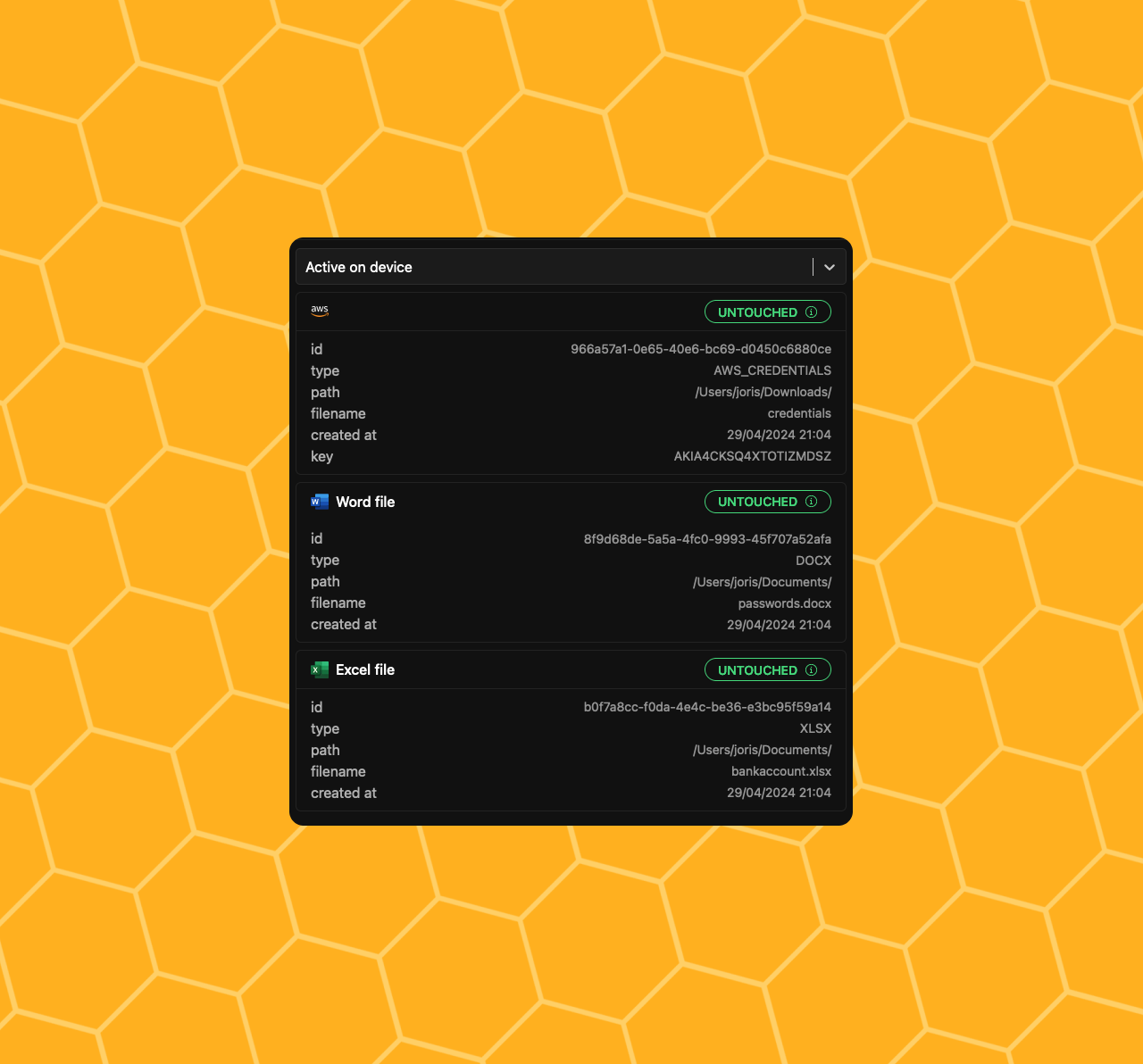
✅ No more Spreadsheets to keep track of the location of your honeytokens. Our dashboard will show you every token that is active / inactive.
🦹🏽 Token rotation: bad-actors might be ignoring the token if it is untouched for too long. We fixed that with token-rotation, which will keep your tokens fresh.
Get started for freeBuilt for seamless integration with your existing solutions
🔑 Login with SSO: Honeyhack integrates with all major Identity Providers.
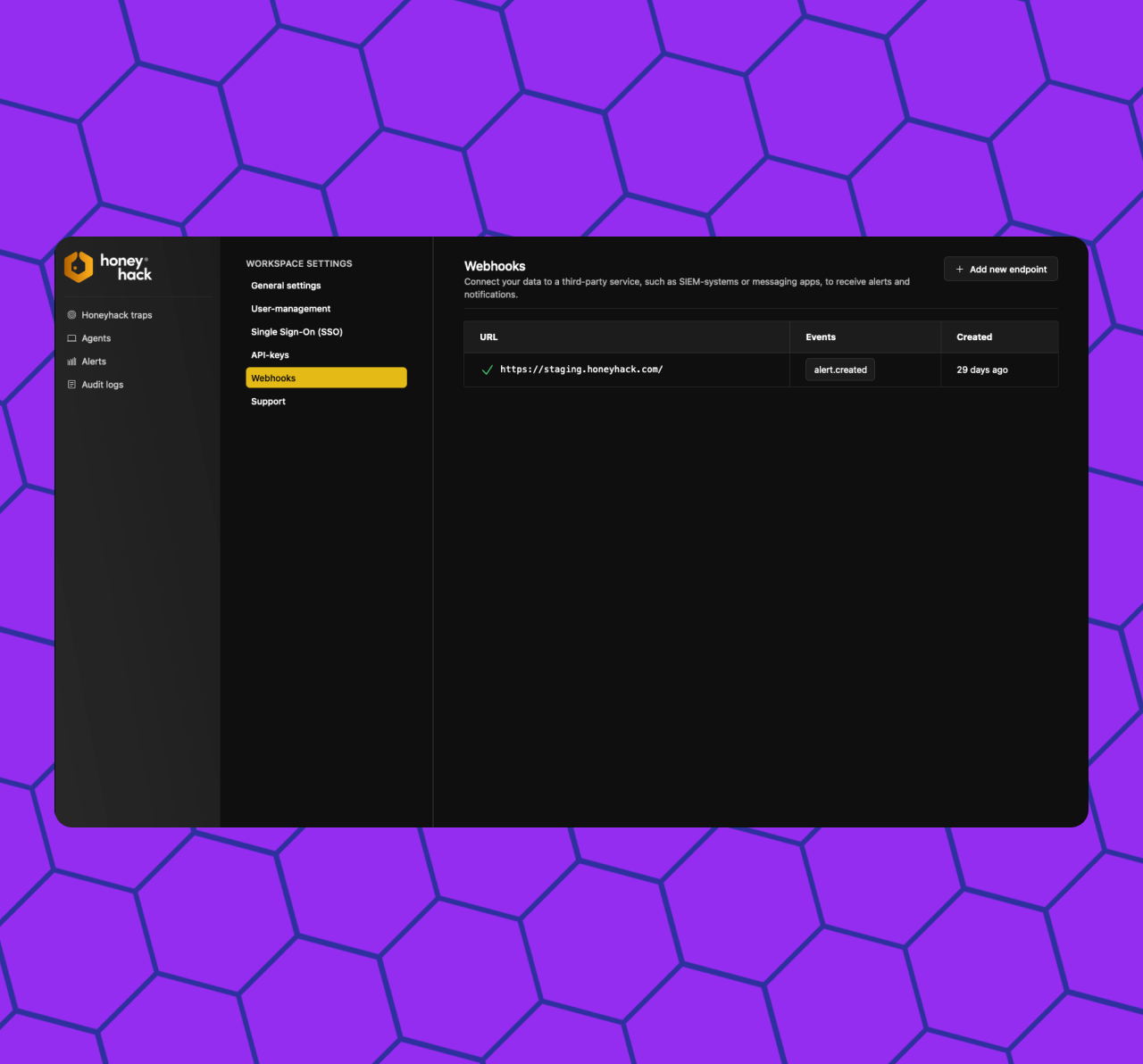
🪝 Webhooks: Sent events to your XDR / SIEM / EDR / SOAR.
Frequently asked questions
What is the pricing?
Our pricing plans are based on the number of endpoints in your organization. This scalable approach ensures that you only pay for what you need, depending on the size and scope of your infrastructure. For a detailed quote, please contact us directly.
Is Honeyhack effective?
Yes, HoneyHack effectively identifies unauthorized access and security threats by deploying honeypots and honeytokens that mimic real systems. This proactive method allows for early detection and swift response, enhancing your cybersecurity measures.
Do you offer a free trial?
Yes, we offer a free trial. Please contact us directly for more details on how to get started and experience the benefits of our honeypot and honeytoken solutions firsthand.
Do you have an enterprise-plan
Yes, we offer an enterprise plan tailored to meet the needs of larger organizations. Please call us for more information and to discuss how we can best support your specific security requirements.
Can I partner with Honeyhack?
Yes, we welcome partnership inquiries, especially from cybersecurity companies looking to enhance their offerings with deception technology. If you're interested in integrating honeypots and honeytokens into your security stack, please contact us to discuss potential collaborations.
Is Honeyhack safe?
Yes, HoneyHack is safe. Our commitment to safety is reflected in our diligent software development process and our aim to be ISO 27001 compliant, ensuring that our security measures adhere to high international standards. This rigorous approach guarantees that our honeypots and honeytokens operate securely within your infrastructure.
